HP Inc. has unveiled its latest Threat Insights Report. The document highlights cybercriminals’ fast-changing tactics and explains how attackers increasingly use malware kits and generative artificial intelligence (GenAI) to lower the barriers to cybercrime.
The use of these advanced tools is reshaping the threat landscape. Cybercriminals now require less effort and skill to launch attacks. This shift means organizations must act swiftly to counter these evolving threats.
Malware kits and GenAI streamline the design and deployment of malicious software. These tools let attackers build effective infection chains quickly, and even inexperienced individuals can now launch dangerous campaigns.
HP researchers identified large campaigns relying on standard loaders and techniques. For instance, attackers embed malicious code into image files hosted on platforms like archive.org.
This approach helps them evade detection by appearing benign to web proxies and other network security tools.
Generative AI has become a powerful enabler of cybercrime. HP researchers observed its use in campaigns employing HTML smuggling. Attackers used GenAI to craft malicious HTML documents, which included professional layouts and detailed instructions, that delivered XWorm remote access trojans (RATs).
This technology allows attackers to iterate on their malicious code rapidly. It also reduces the skill needed to produce sophisticated attacks. GenAI’s influence is making it easier for cybercriminals to outpace security defenses.
Another alarming trend involves the gaming community. Cybercriminals are targeting video game cheat tools and modification repositories. On platforms like GitHub, attackers embed malware like Lumma Stealer into these repositories.
Lumma Stealer focuses on harvesting sensitive data. It targets passwords, crypto wallets, and browser information. Many gamers deactivate security tools to use cheats, increasing their risk of infection.
HP’s report also provides a breakdown of standard attack methods. Executables remain the most widespread malware delivery format, making up 40 percent of threats. Archive files come second, accounting for 34 percent.
Among these, .lzh files have sharply increased, especially in attacks targeting Japanese-speaking users.
This data highlights cybercriminals’ adaptability. They frequently shift techniques to bypass security measures.
Reducing the attack surface is critical. Instead of relying on detection-based tools, organizations should focus on prevention. Isolating high-risk activities, such as opening email attachments, is practical.
HP Wolf Security plays a key role in combating these threats. Its hardware-enforced isolation technology ensures that risky tasks run in secure virtual environments. This method contains potential threats without impacting productivity.
The platform has safely analyzed over 65 billion potentially malicious files. No reported breaches have occurred in systems protected by HP Wolf Security. By safely detonating malware, the platform captures detailed insights into its behavior.
The report also highlights gaps in existing defenses. Around 11 percent of email threats bypassed one or more email gateway scanners. This finding underscores the importance of robust endpoint security solutions that address vulnerabilities detection-based systems miss.
Organizations must adopt a multi-layered defense strategy. Combining isolation technologies with real-time threat intelligence is crucial, as this approach ensures higher protection against sophisticated attacks.
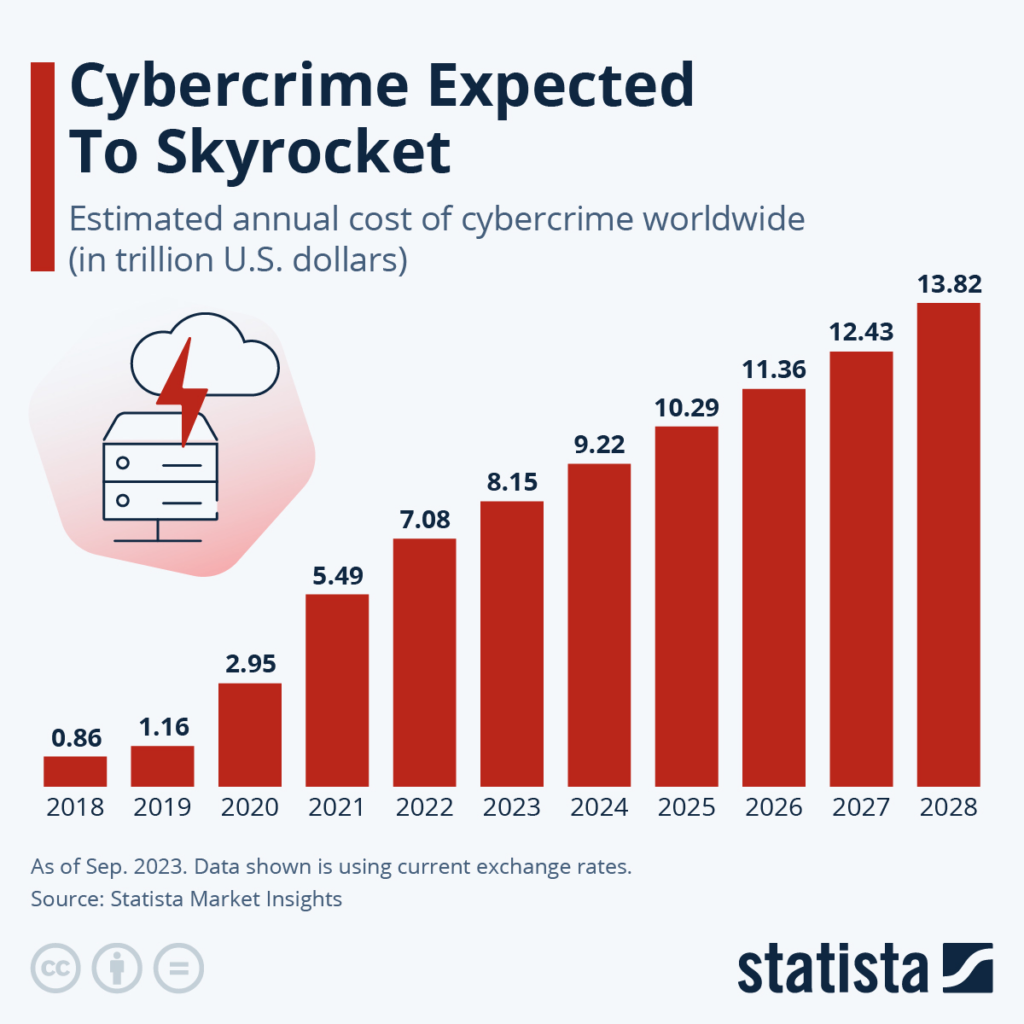
The findings emphasize the growing threat posed by commodified cybercrime tools. Even low-skill attackers can now launch effective campaigns. GenAI further amplifies this risk by simplifying the creation of malicious code.
Businesses and individuals must take proactive measures to counter these threats. Advanced isolation technologies can help mitigate risks. Reducing the attack surface and investing in robust security solutions are essential.
The rapid evolution of cybercrime tactics demands urgent action. Organizations must shift their focus from detection to containment to effectively neutralize sophisticated attacks.
Organizations can protect themselves by staying informed and adopting proactive measures. The HP Threat Insights Report reminds us of the need for constant vigilance.
Cybercriminals will continue to innovate, but their impact can be minimized with the right strategies.
- 107shares
- Facebook Messenger
About the author
Andrew Chavez is a passionate technology researcher and MSc graduate from Texas A&M University. He has a broad range of knowledge on current tech developments, new discoveries in the field of high-tech and science, as well as software engineering proficiency. With an insatiable appetite for learning and discovering, Andrew strives to bridge the gap between academia and industry. His ambition drives him to make meaningful contributions to the tech world continuously.